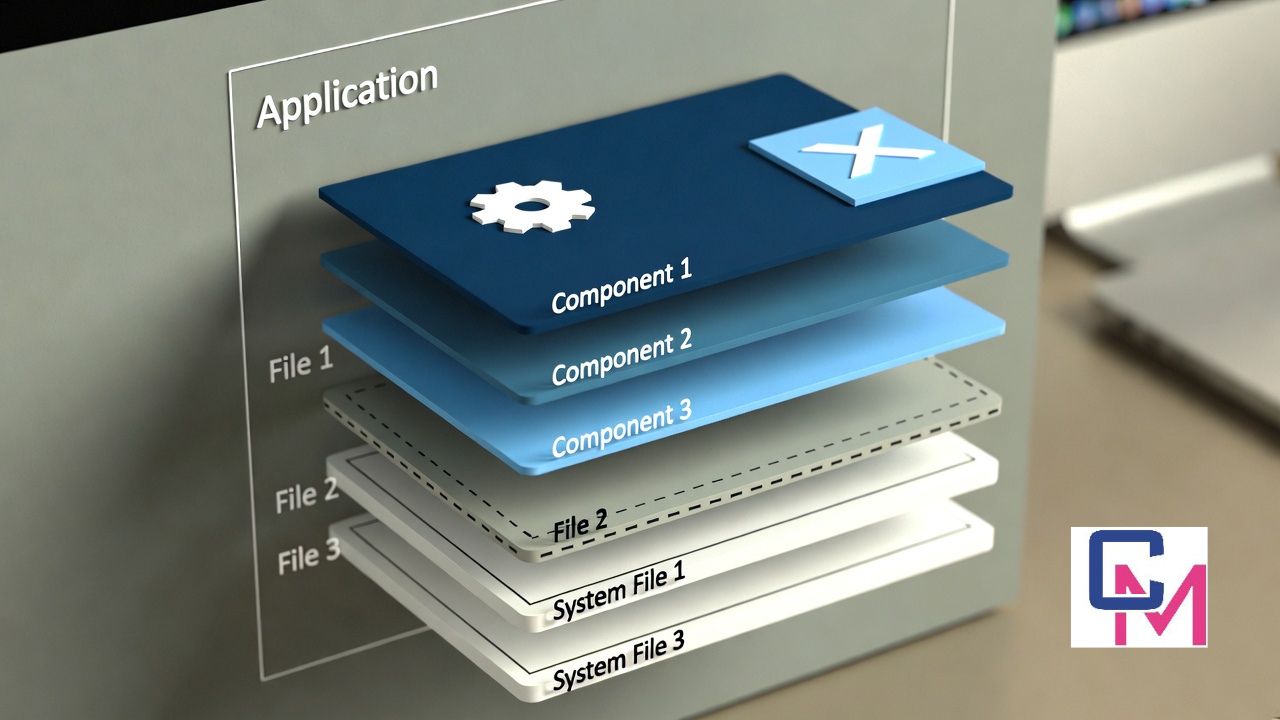
Not every piece of software arrives with a polished brand name, a well-designed website, or a clearly defined purpose. Sometimes a term appears quietly—in a file list, a background process, a download folder, or an online discussion—and immediately raises questions because it doesn’t look familiar or self-explanatory.
Software keepho5ll is one such name. Many users encounter it unexpectedly and begin searching for answers. Is it a real application? Is it safe? Why does it appear at all? These questions are reasonable, especially in a digital environment where clarity and trust matter.
This article takes a calm, well-researched, and human approach to understanding software keepho5ll—what it may represent, how people are encountering it, and how to think clearly about unfamiliar software without jumping to conclusions.
What Is Software keepho5ll?
At present, software keepho5ll does not appear to be a widely documented or mainstream application with a clearly identifiable publisher or long public history. Instead, it functions more like a label that users notice and then investigate.
In many cases, such software names fall into a gray area:
- They may belong to small or niche tools with limited distribution.
- They may be internal or system-generated identifiers mistaken for full applications.
- They may be filenames or components rather than standalone programs.
This lack of clarity does not automatically suggest danger. It simply means the software does not come with the usual signals people expect, such as a recognizable brand or detailed public documentation.
Where Software keepho5ll Might Come From
Unfamiliar software names can emerge from multiple sources, and understanding these possibilities helps avoid unnecessary alarm.

Niche or Limited-Release Software
Some tools are developed for specific use cases, organizations, or small user groups. These projects may never appear in popular app stores or major software directories. When users outside that circle encounter the name, it naturally feels obscure.
System or Installer Artifacts
In many cases, what users think of as “software” is actually a file, module, or helper component created during an installation process. These components may carry autogenerated or shortened names that were never meant to be seen or interpreted by end users.
Bundled Components
Occasionally, software arrives bundled with other applications. Users may not notice each individual component being installed, only discovering it later in a system list. This can create confusion, especially when the name is unfamiliar.
Important perspective: An unusual name is a reason to investigate—not a reason to panic.
Why Software keepho5ll Is Appearing Online
The visibility of software keepho5ll is driven largely by curiosity rather than confirmed popularity.

User Curiosity
When people see something unfamiliar on their system, they search for it. As more people do this, the term begins to appear more frequently in search results and discussions.
Search Momentum
Search platforms tend to amplify repeated queries. Once a keyword shows consistent interest, it gains momentum, making it seem more widespread than it actually is.
Repetitive Content
As articles are written to explain the term, later content often echoes earlier descriptions. Over time, this repetition creates the appearance of authority, even when the original information was limited.
How Software keepho5ll Is Being Used
Public descriptions of software keepho5ll vary, which suggests that usage is not clearly standardized.

Claimed Functional Use
Some descriptions present it as a tool related to organization, management, or workflow support. These explanations often sound similar to common productivity software, using familiar terms such as efficiency, structure, or task handling.
However, descriptions alone do not confirm functionality. Without clear documentation or verified distribution channels, these claims should be treated as unconfirmed.
Real-World Discovery
More commonly, users report encountering software keepho5ll unexpectedly—after a download, during system checks, or while reviewing installed items. This moment of discovery, rather than active adoption, is what triggers concern.
Common User Questions
When people search for software keepho5ll, they usually want simple answers:
- What is it?
- Do I need it?
- Is it safe to keep?
- Can I remove it?
These questions reflect a desire for control and understanding rather than fear.
Is Software keepho5ll Legitimate or Safe?
There is no single answer that applies to every situation. Safety depends on context.
H3: Look at the Source
If the software came from a trusted installer, known platform, or professional environment, it may simply be a supporting component. If it appeared without explanation, further checks are reasonable.
H3: Observe System Behavior
Names can be misleading. Behavior matters more. Software that operates transparently, does not demand unnecessary permissions, and does not interfere with normal system settings is generally less concerning than software that behaves aggressively or secretly.
H3: Use Built-In Protections
Modern operating systems provide warnings and protections when unfamiliar applications try to run. Paying attention to these alerts helps users make informed decisions without overreacting.
Professional reminder: Safety is about patterns, not assumptions.
How to Research Software keepho5ll Responsibly
Responsible research is structured and calm.
Start With Context
Think back to when and where the software appeared. Was it associated with another program? Did it arrive after a specific action? Context often explains more than speculation.
Avoid Overconfident Claims
Many online explanations sound certain but provide little verifiable detail. Treat confident language without evidence with caution.
Keep Testing Controlled
If deeper analysis is needed, testing unknown software in a controlled or isolated environment is safer than experimenting on a primary system.
Software keepho5ll in the Bigger Software Landscape
The appearance of names like software keepho5ll reflects a broader reality of modern computing. Systems generate countless files, identifiers, and components that are essential for operation but invisible to most users. When these elements become visible, they feel unfamiliar—even though they may be routine.
This gap between machine logic and human understanding is where confusion arises.
What You Should Know Before Making Assumptions
The most important takeaway is restraint.
A name alone does not define intent, quality, or safety. Clear thinking requires:
- checking origin,
- observing behavior,
- and avoiding conclusions based on appearance alone.
When users stay methodical, uncertainty becomes manageable.
Conclusion
Software keepho5ll represents a category of modern digital experiences where unfamiliar labels surface and prompt investigation. Its presence does not automatically indicate usefulness or risk. What matters is how it arrived, how it behaves, and whether it serves a purpose you recognize.
By approaching such software with curiosity rather than fear, users maintain control and confidence. Understanding grows not from dramatic assumptions, but from careful observation and informed judgment.
In the end, clarity is the best tool—and it begins with asking the right questions calmly and thoughtfully.
The Story Behind hj54kyf and What You Should Know
FAQs
What is software keepho5ll?
Software keepho5ll is an unfamiliar software label that users often notice on their system or online and then research for clarity. It does not have a widely recognized public identity, which is why it raises questions rather than offering immediate understanding.
Why did software keepho5ll appear on my device?
It may have arrived as part of another installation, a system-related component, or a bundled file. In many cases, users encounter such names without intentionally installing them.
Is software keepho5ll safe to keep?
Safety depends on context. If it came from a trusted source and shows no unusual behavior, it may be harmless. If its origin is unclear or it behaves unexpectedly, further verification is a sensible step.
Can I remove software keepho5ll if I don’t recognize it?
If you are unsure about its purpose, you can remove it cautiously using standard system tools. Always make sure it is not a required system component before deleting it.
Why is there so little clear information about software keepho5ll online?
Some software names are niche, internal, or autogenerated, meaning they are not supported by detailed public documentation. This lack of information often leads to curiosity-driven searches.